LEONARDTOWN, Md. (March 29, 2016)—MedStar St. Mary's Hospital in Leonardtown reported on their Facebook page Monday that their internal computer systems have been impacted by a 'virus that prevents certain users from logging-in to our system.'
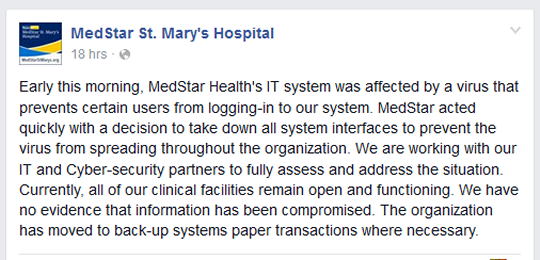
"Early this morning, MedStar Health's IT system was affected by a virus that prevents certain users from logging-in to our system. MedStar acted quickly with a decision to take down all system interfaces to prevent the virus from spreading throughout the organization. We are working with our IT and Cyber-security partners to fully assess and address the situation. Currently, all of our clinical facilities remain open and functioning. We have no evidence that information has been compromised. The organization has moved to back-up systems paper transactions where necessary."
A screen capture purported to be from a screen of a hospital computer is circulating on the internet and identifies the virus as ransomware. Ransomware works by encrypting the computer's disk drives using advanced encryption techniques that require a unique key to unlock. Any attached file systems, such as USB drives and shared network drives can also be impacted. The perpetrators require the victim to pay a ransom in order to obtain the key to unlock their files. Payment is often required to be made in Bitcoin—a relatively new digital currency that is very difficult to trace.
Renowned information security researcher and author Brian Krebs just 2 weeks ago documented a similar attack at Methodist Hospital in Henderson, Kentucky. The attackers demanded $1,600 in ransom in this case. A Los Angeles hospital paid almost $17,000 in ransom in February, according to a NPR report.
Krebs wrote that while many ransomware infections are the result of people browsing the web with outdated browsers and/or browser plug-ins like Adobe Flash and Java, the attack in Kentucky used one of the original methods of infection.
"The attack on Methodist Hospital was another form of opportunistic attack that came in via spam email, in messages stating something about invoices and that recipients needed to open an attached (booby-trapped) file."
While in the past there had been cases of a flaw in the ransomware code that allowed data to be recovered, most security experts today agree that it is essentially impossible to decrypt the files without the key held by the perpetrators. However, many experts disagree on whether or not to pay the ransom. Those against paying argue that payment only encourages the spread of the problem. They also say that payment is no guarantee that you will receive the key. Others counter that to not provide the key to victims who pay would only damage the business model of the perpetrators and encourage others not to pay in the future. The alternative is wipe the affected systems and restore the data from backups—if they exist.


